In our previous blog post “Pentesting with iPhone without Jailbreak” we gave you an overview of software named iFunbox as well as how to access the local storage of any application. In today’s blog post we shall expand on that and we will show you how to leverage that technique and perform a malicious attack.
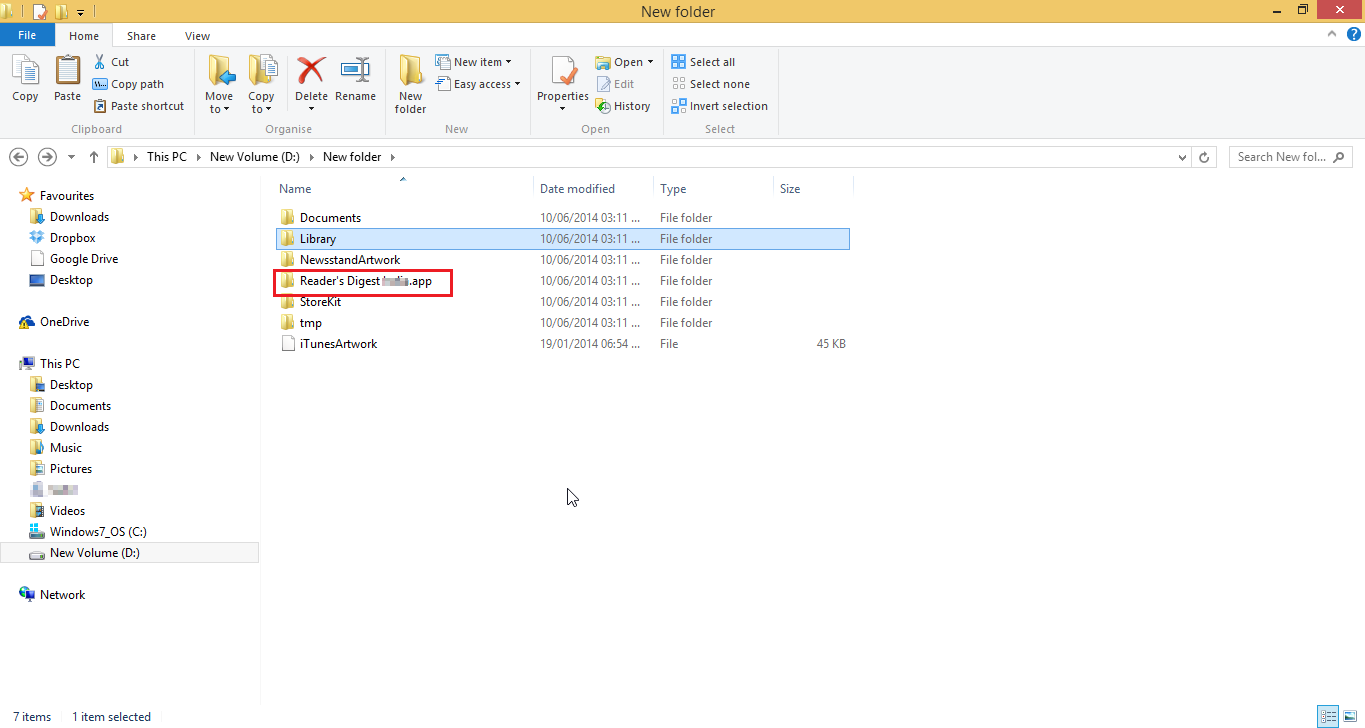
Access the local storage of the application (if you want to know how to access it kindly refer to our previous post.)
Now when an attacker gets access to this local storage he can upload any malicious content into the storage. Also any desired changes to the content of the application can be done. And with the help of the software (ifunbox) we can push the content back into the device. So when a user opens the application the malicious content will also be loaded along with the application.
Let us take a scenario in which an application stores certain offline webpages for faster loading of its application. Now an attacker who has the access to the local storage can insert malicious JavaScript into these pages and push (use the option “Copy from PC” in the ifunbox) the application back into the phone. Now whenever a user runs that application the JavaScript’s will also run and in this way he can take control of the device.
The above image shows a cross site scripting attack we performed on an application by exploiting application's local storage. The interesting thing here is that all the applications store something in local storage i.e. offline pages, images, sensitive data etc. Hence there is lot for an attacker to exploit. Also one might think that in terms of security the device is pin locked and fingerprint locked but sadly these attacks would even work if the device was protected with such security mechanisms.
To curb such attacks the most important thing one could do to safe guard would be “Keep your phone with you at all times ;-)” .
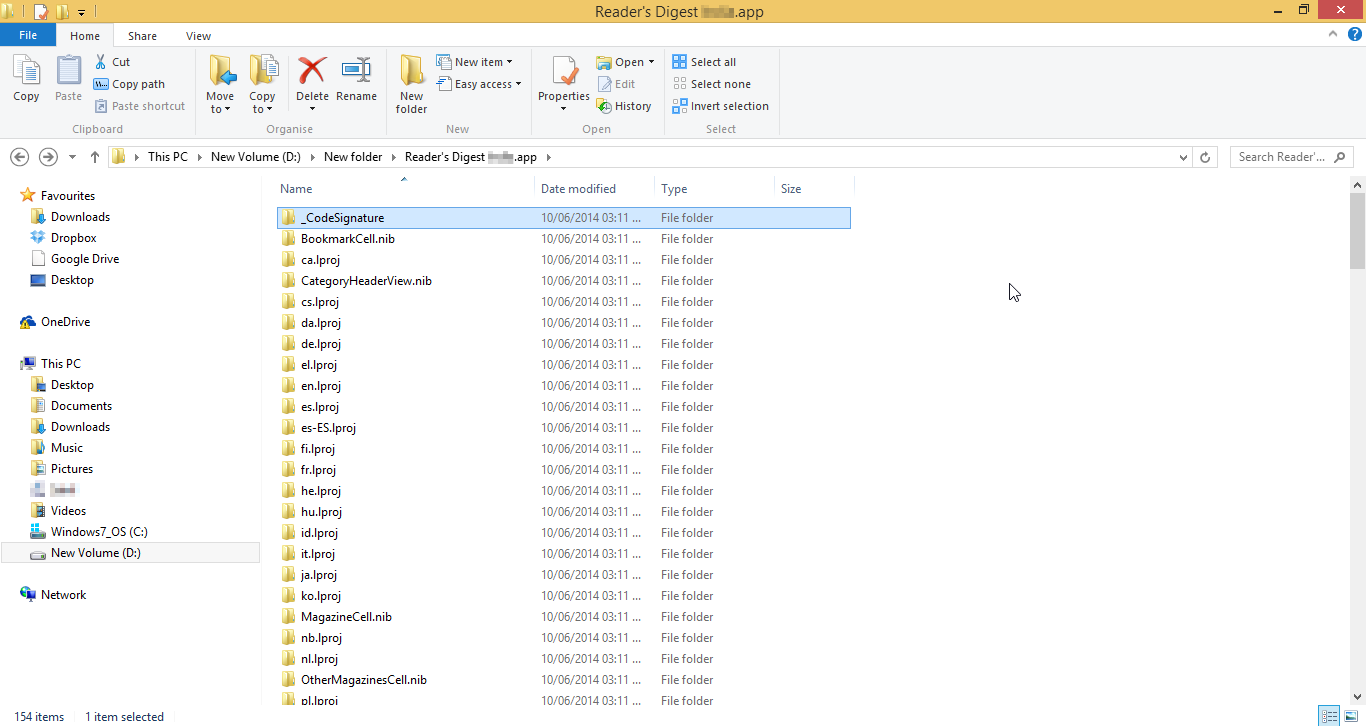
Note:- All the changes are to be made outside the ".app" folder.
Note:- All the changes are to be made outside the ".app" folder.